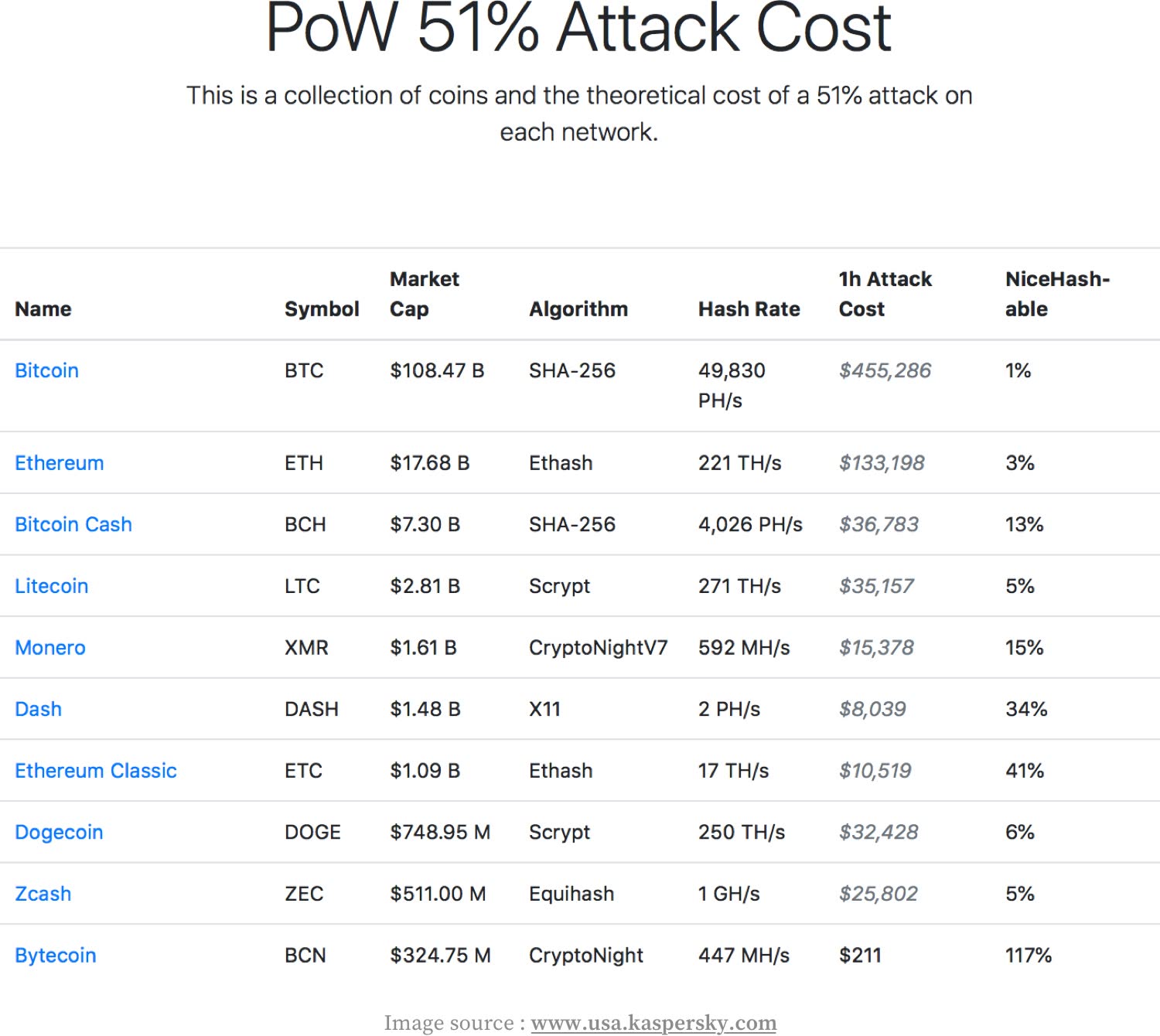
Blockchain and cryptocurrency are relatively new advancements, but with it comes newer threats and security concerns. One of the biggest risks in the case of cryptocurrency is exchange hacking. Most of these hacks happen on centralized exchanges, which, although more vulnerable than decentralized exchanges, continue to be popular nonetheless because of their ease of use.
Crypto Hacks: An Overview In Numbers
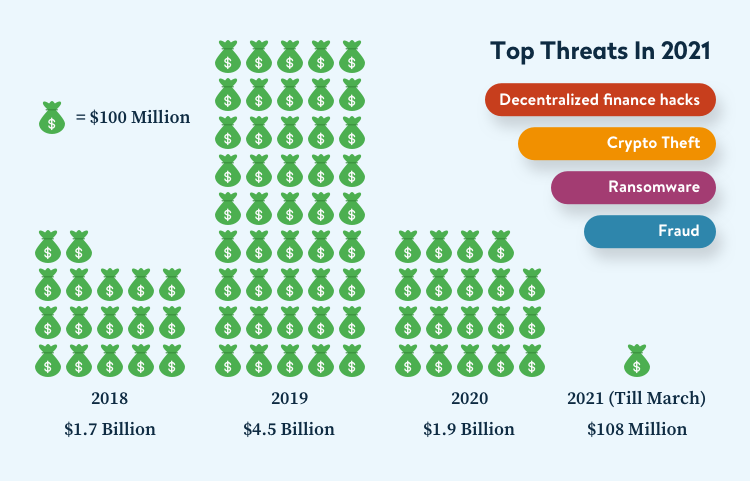
Major Crypto Hacks Over The Years
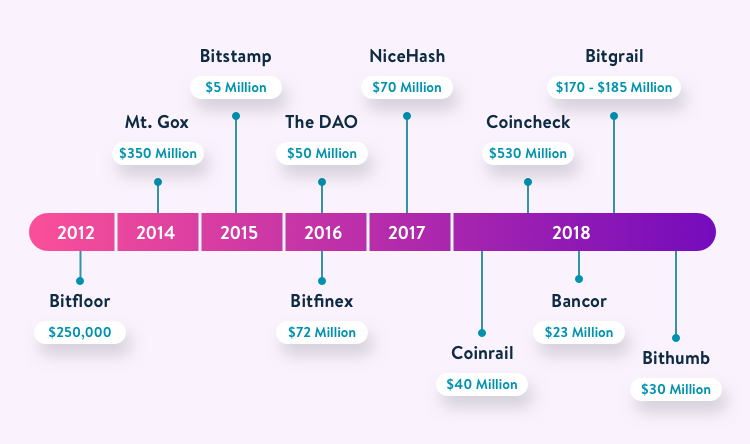
This brings to focus the issue of security threats in cryptocurrency. Let’s take a look at five of the biggest crypto hacks in history, and what one can do to stay safe from such attacks.
- BitCoin (2010)
Bitcoin should have died as quickly as it was born when in August 2010, a hacker was able to mine 184.467 billion bitcoins thanks to a value overflow error in the code. This is now known as the “Value Overflow Incident”. Luckily, the issue was identified by the bitcointalk community in five hours. A permanent solution was provided to fix the issue and prevent any future instances of it. - Mt. Gox (2014)
Mt. Gox was once the largest bitcoin exchange in the world, handling 70% of all transactions. Unfortunately, it was hacked twice. In June 2011, a hacker was able to access Mt Gox auditor’s credentials and transfer 2609 Bitcoins to an address for which Mt. Gox had no keys. The second, much more massive attack, however, destroyed Mt. Gox. In 2014, anywhere between 750,000-850,000 BTCs (worth $350mn – $450mn at the time) went missing from the exchange, as investors lost their money and Mt. Gox filed for bankruptcy. - Bitfloor (2012)
In 2012, a bunch of hackers gained access to Bitfloor’s unencrypted private keys that were stored online for backups. They were able to swindle 24,000 BTC (worth $250,000 at the time). This was enough to shut the exchange down, as it had lost most of its capital and its banks refused to do further business thanks to regulatory measures, and customers lost all their money. - The DAO (2016)
A decentralized autonomous organization, (DAO) operates as a large, unified venture capital company where users can invest and then vote on which projects they want to fund. Ethereum rather confusingly named its DAO “The DAO”. On 18 June 2016, a hacker was able to exploit a loophole to create a “child DAO”. This enabled the hacker to create infinite withdrawal requests to the same DAO tokens. Using this loophole, the hacker drained over 3.5 million Ether (worth $50mn at the time) into the child DAO, leading to the creation of Ethereum Classic. - Bitfinex (2016)
Bitfinex was also a company that was hacked twice. In 2015, 1500 BTC were stolen. But the larger attack came in 2016: 120,000 BTC, worth $72mn, were stolen from the exchange. The hackers exploited a vulnerability in the multisignature wallet architecture of Bitfinex and BitGo, which let them enable approval and withdrawal of coins from hot wallets. Bitfinex bounced back through a series of measures: distributing the losses among users, compensating the users’ losses with BFX (which were redeemable in USD), and so on, and continues to operate today with one of the biggest USD/BTC volumes in the world.
What Is The Situation Now
A 51% attack on an exchange right now is part of the features the technology offers, and although exchanges are trying to minimize the possibility of it through various measures, it is impossible to say with certainty that another attack will never happen, which is why it’s important to stay safe as a user.
How can you protect yourself?
Most of these hacks happen on centralized crypto exchanges, which store users’ private keys. Anyone with access to these private keys can immediately own the cryptocurrency funds. Additionally, most crypto traders keep their assets on the exchange in a hot wallet, as they want to react quickly while trading. Hot wallets are much more vulnerable than cold storage, and storing the profits from transactions made on an exchange on the very same exchange is not a safe idea. Data storage on exchanges also needs to be encrypted more stringently, and exchange servers and their features need to be audited periodically. So as a user:
- Store a majority of your cryptocurrency in cold storage.
- Handle your private keys and public addresses carefully.
- Use decentralized exchanges instead.
The key is to remember that the threats and vulnerabilities do not outweigh the importance of blockchain technology and cryptocurrency, and there are thousands of possibilities for what we can do with it. If you or your business have tech projects involving blockchain, talk to the best in the space right now: CodeGlo. Talk to us now.
Disclaimer: This article is NOT financial advice, investment or otherwise.